“If a hacker can compromise your business in just 10 minutes, how prepared are you to stop him? A cyber attack occurs every 39 seconds—how well-equipped is your Security Operations Centre (SOC) to address this challenge?
Table of Contents
ToggleTable of Contents
What is SOC Cyber Security?
SOC (Security Operations Centre) is a centralised unit that protects your business from cyber threats 24/7. It detects, investigates, and mitigates advanced attacks by hackers.
Real-World Fact: “95% of cyberattacks happen due to human error. If your business lacks a Security Operations Centre (SOC), it becomes vulnerable to cybercriminals.

What is the significance of SOC, and why is it essential for every business?
If your business participates in these activities, then you require a SOC.
- Store sensitive customer data (PII).
- Operate financial transactions or eCommerce.
- Have cloud-based services or remote employees.
- I want to maintain ISO 27001 or SOC 2 compliance.
Example: A data breach cost an eCommerce website $3.5 million in 2023. If they had a SOC, this attack could have been detected earlier!
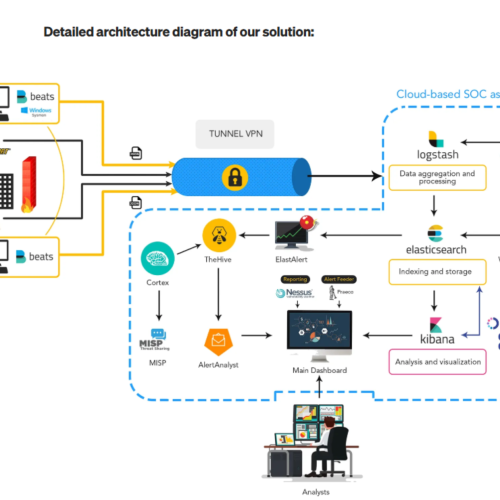
How does a SOC work?
SOC’s 4-Step Process:
- Threat detection and monitoring: AI-powered SIEM and IDS tools detect unusual network activities.
- Threat Analysis & Investigation: Security analysts manually review alerts to filter out false positives.
- Incident Response & Mitigation: If the threat is confirmed, the SOC isolates and neutralises it.
- Threat Intelligence & Prevention: Advanced threat intelligence is used to prevent future attacks.
Example:The DarkSide ransomware attack targeted the Colonial Pipeline in 2021. Their SOC could have stopped this attack if they had used better threat intelligence.
SOC Components—Work of Every Layer
A strong SOC has multiple components:
🔹 Network Security Monitoring: Firewalls and IDS/IPS provide security.
🔹 Endpoint Security: EDR and antivirus solutions detect malware.
🔹 Threat Intelligence & Hunting: Advanced APT detection and forensics tools are used.
🔹 Cloud Security: Zero-trust architecture and CASB (Cloud Access Security Broker) solutions.
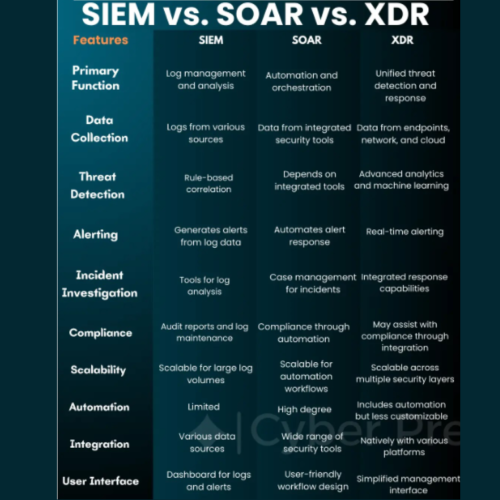
SOC vs. SIEM—What is the Difference?
Security Operations Center (SOC) and Security Information and Event Management (SIEM) are both critical components of an organization’s cybersecurity infrastructure, but they serve different purposes and functions. Here’s a detailed comparison:
1. Definition and Purpose
-
SOC (Security Operations Center):
-
A SOC is a centralized unit or team responsible for monitoring, detecting, analyzing, and responding to cybersecurity incidents in real-time.
-
The primary purpose of a SOC is to provide continuous security monitoring and incident response to protect an organization’s assets, data, and infrastructure from cyber threats.
-
-
SIEM (Security Information and Event Management):
-
SIEM is a technology platform that aggregates, correlates, and analyzes security-related data from various sources across an organization’s IT infrastructure.
-
The primary purpose of SIEM is to provide a comprehensive view of an organization’s security posture by collecting and analyzing log data, identifying potential security incidents, and generating alerts.
-
2. Scope and Functionality
-
SOC:
-
People: The SOC is staffed by cybersecurity professionals, including analysts, engineers, and incident responders.
-
Processes: The SOC follows defined processes and procedures for monitoring, incident detection, investigation, and response.
-
Technology: The SOC uses various tools, including SIEM, intrusion detection systems (IDS), endpoint detection and response (EDR), and threat intelligence platforms.
-
Activities: The SOC is responsible for real-time monitoring, threat hunting, incident investigation, forensic analysis, and coordinating incident response efforts.
-
-
SIEM:
-
Data Aggregation: SIEM collects and aggregates log data from various sources, such as firewalls, servers, endpoints, and applications.
-
Correlation and Analysis: SIEM correlates events from different sources to identify patterns that may indicate a security incident.
-
Alerting: SIEM generates alerts based on predefined rules, anomalies, or suspicious activities.
-
Reporting and Compliance: SIEM provides reporting capabilities for compliance with regulatory requirements and internal security policies.
-
3. Key Components
-
SOC:
-
Team: Security analysts, incident responders, threat hunters, and SOC managers.
-
Tools: SIEM, IDS/IPS, EDR, threat intelligence feeds, and forensic tools.
-
Processes: Incident response plans, playbooks, and escalation procedures.
-
-
SIEM:
-
Data Sources: Logs from firewalls, servers, endpoints, applications, and network devices.
-
Correlation Engine: Analyzes and correlates events to detect potential threats.
-
Dashboards and Reporting: Provides visualizations and reports for security monitoring and compliance.
-
4. Interaction and Integration
-
SOC and SIEM Interaction:
-
The SOC relies heavily on SIEM as a core tool for monitoring and detecting security incidents. SIEM provides the SOC with the necessary data and alerts to perform its functions effectively.
-
The SOC uses SIEM to centralize and analyze security data, enabling faster detection and response to threats.
-
-
Integration:
-
SIEM integrates with various security tools and data sources to provide a comprehensive view of the organization’s security posture.
-
The SOC integrates SIEM with other tools like EDR, threat intelligence platforms, and incident response systems to enhance its capabilities.
-
5. Focus and Output
-
SOC:
-
Focus: The SOC focuses on the operational aspects of cybersecurity, including real-time monitoring, incident detection, and response.
-
Output: The SOC produces incident reports, threat intelligence, and post-incident analysis to improve the organization’s security posture.
-
-
SIEM:
-
Focus: SIEM focuses on data collection, correlation, and analysis to identify potential security incidents.
-
Output: SIEM generates alerts, reports, and dashboards that provide insights into the organization’s security events and compliance status.
-
6. Challenges
-
SOC:
-
Resource Intensive: Requires skilled personnel, continuous training, and significant investment in tools and infrastructure.
-
Alert Fatigue: High volume of alerts can lead to alert fatigue, making it challenging to prioritize and respond to incidents effectively.
-
-
SIEM:
-
Complexity: SIEM systems can be complex to configure and manage, requiring expertise to tune rules and reduce false positives.
-
Data Volume: Handling large volumes of log data can be challenging, requiring robust infrastructure and storage solutions.
-
7. Complementary Roles
-
SOC and SIEM are complementary:
-
SIEM provides the data and alerts that the SOC needs to detect and respond to threats.
-
The SOC uses SIEM as a critical tool in its arsenal but also relies on other tools, processes, and human expertise to effectively manage and respond to security incidents.
-
Example: If a breach occurs in an organization’s firewall, SIEM will only issue an alert; however, SOC will analyse this alert and take steps to mitigate the breach.
There are 2 types of SOC:
- In-House SOC: $500,000 – $1M annually
- Managed SOC Services: $3,000 – $15,000 monthly
Example: An SMB company chose Managed SOC service and prevented financial fraud of $50,000 by investing just $500/month.
Future of SOC—New Era of AI & Automation
AI- and automation-based SOCs will become ubiquitous in the coming times. Next-gen SOC features:
- AI-Driven Threat Detection
- Automated Incident Response
- Predictive Cyber Threat Intelligence
Example: Google’s Chronicle Security has already implemented the AI-based SOC 2.0 model for intelligent threat hunting.

FAQs
1. What is SOC 2 compliance?
Answer:
SOC 2 (Service Organization Control 2) is a cybersecurity framework developed by the American Institute of CPAs (AICPA). It ensures that organizations securely manage and protect customer data by adhering to strict standards for security, availability, processing integrity, confidentiality, and privacy. SOC 2 compliance is often required for businesses that handle sensitive customer information, such as cloud service providers.
2. Can small businesses get an affordable SOC solution?
Answer:
Yes, small businesses can access affordable SOC solutions through Managed SOC Services. These services provide outsourced security monitoring, threat detection, and incident response at a fraction of the cost of building an in-house SOC. Managed SOC providers use advanced tools like SIEM and offer scalable solutions tailored to the needs and budgets of small businesses.
3. What is the difference between SOC 1, SOC 2, and SOC 3?
Answer:
-
SOC 1: Focuses on financial reporting controls and is relevant for organizations that impact their clients’ financial statements.
-
SOC 2: Focuses on data security, availability, processing integrity, confidentiality, and privacy. It is widely used for technology and cloud service providers.
-
SOC 3: Similar to SOC 2 but provides a general-use report without detailed information, making it suitable for public distribution.
4. What is the role of a SIEM in a SOC?
Answer:
A SIEM (Security Information and Event Management) is a core tool used by a SOC to collect, correlate, and analyze security data from across an organization’s IT infrastructure. It helps detect potential threats, generate alerts, and provide insights into security incidents. The SOC team uses SIEM to monitor and respond to threats in real-time.
5. What are the key benefits of having a SOC?
Answer:
-
Proactive Threat Detection: Continuous monitoring helps identify and respond to threats before they cause significant damage.
-
Incident Response: A SOC provides a structured approach to investigating and mitigating security incidents.
-
Compliance: Helps organizations meet regulatory and industry compliance requirements.
-
Threat Intelligence: Leverages real-time threat data to stay ahead of emerging risks.
-
Cost Efficiency: Reduces the financial impact of breaches by minimizing downtime and data loss.
6. What is the difference between a SOC and a NOC (Network Operations Center)?
Answer:
-
SOC (Security Operations Center): Focuses on cybersecurity, including threat detection, incident response, and vulnerability management.
-
NOC (Network Operations Center): Focuses on network performance, uptime, and infrastructure management. While a NOC ensures the network is running smoothly, a SOC ensures it is secure from cyber threats.
7. How does a SOC handle false positives?
Answer:
A SOC uses advanced tools like SIEM with machine learning and AI to reduce false positives. Analysts also fine-tune detection rules, prioritize alerts based on severity, and conduct thorough investigations to distinguish between false positives and real threats.
8. What is the difference between SOC 2 Type I and Type II?
Answer:
-
SOC 2 Type I: Evaluates the design of an organization’s controls at a specific point in time.
-
SOC 2 Type II: Assesses the operational effectiveness of those controls over a period of time (usually 6-12 months). Type II is more comprehensive and provides greater assurance to stakeholders.
9. Can a SIEM replace a SOC?
Answer:
No, a SIEM cannot replace a SOC. While a SIEM is a critical tool for collecting and analyzing security data, it requires human expertise to interpret alerts, investigate incidents, and respond effectively. A SOC provides the people, processes, and additional tools needed to manage cybersecurity operations.
10. What industries benefit most from SOC 2 compliance?
Answer:
Industries that handle sensitive customer data, such as cloud computing, SaaS (Software as a Service), healthcare, finance, and e-commerce, benefit most from SOC 2 compliance. It demonstrates a commitment to data security and builds trust with customers and partners.
Does your business want to adopt SOC?
Cyber threats are increasing day by day. If you want your business to be safe, then SOC is not just an option but a necessity.
